NetFlow can be enabled on Catalyst 6500 Switches with a Supervisor Engine 32, RSP 720 or a Supervisor Engine 720. NetFlow cache on the Multilayer Switch Feature Card (MSFC) captures statistics for flows routed in software and the NetFlow cache on the Policy Feature Card (PFC) captures statistics for flows routed in hardware. The configuration of Netflow neither disrupts the traffic nor disables the configured interface.
To start first install NetFlow Analyzer (or similar tool) on your PC so that your PC becomes a NetFlow Collector. Do note the port number (e.g.: 9996) used by you NetFlow Analyzer Application. With the data obtained NetFlow Collectors can generate reports and statistics of traffic flowing through the switch or router.
Next on the Catalyst 6500 configure NetFlow to enable NetFlow on both the MSFC and PFC, so that it can send the Netflow information to the NetFlow Collector. You also need to configure the NetFlow Data Export (NDE) on the switch in order to export the NetFlow statistics to the NetFlow collector. Assuming the NetFlow Collector IP Address is 172.16.16.1, the following configuration has to be made
ip flow-export destination 172.16.16.1 9996
ip flow-export source Loopback 0
ip flow-export version 5
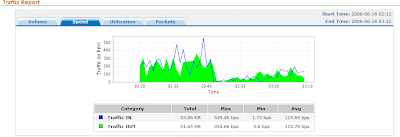
To avoid spikes in the traffic report, use the ip flow-cache time active N command (where N can be from 1 to 60 minutes). The default is 30 minutes, which can lead to having spikes in your traffic report. It is important to set this value to 1 minute to generate alerts and view troubleshooting data.
ip flow-cache timeout active 1
On interfaces that need to be monitored, enter the ip route-cache command. Enabling ip route-cache on the interface enables NetFlow on the MFSC. On 6500 12.2SXH Release, NetFlow is enable on the Layer 3 interface using ip flow ingress command on the interface.
To enable NetFlow & NDE for Layer 2
interface vlan 10
ip route-cache
!
interace GigabitEthernet 1/1
ip route-cache
To enable NetFlow on the PFC, enter the mls netflow command and to configure flow mask on the PFC, configure mls flow ip interface-full. Apply ip flow ingress layer2-switched vlan 10,20 command to enables NetFlow and NDE for Layer 2-switched traffic (for ingress-bridged traffic) on the PFC. Should note that NetFlow does not show statistics of traffic that goes across the same VLAN and hence cannot be configured on a layer 2 interface.
Once configured, the interfaces in the NetFlow tool will be shown as ifindex instead of the actual interface name. To obtain the actual interface names the NetFlow tool will have to pull it from the switch SNMP MIB values, therefore you will have to configure SNMP on the NetFlow Collector as well as on the Catalyst 6500 Switch.
access-list 99 permit 172.16.16.1
!
snmp-server group GRPName v3 auth
snmp-server user snmp_username GRPName v3 auth md5 user_authpwd
snmp-server user snmp_username GRPName remote 172.16.16.1 v3 auth md5 user_authpwd access 99
snmp-server host 172.16.16.1 traps version 3 auth snmp_username
